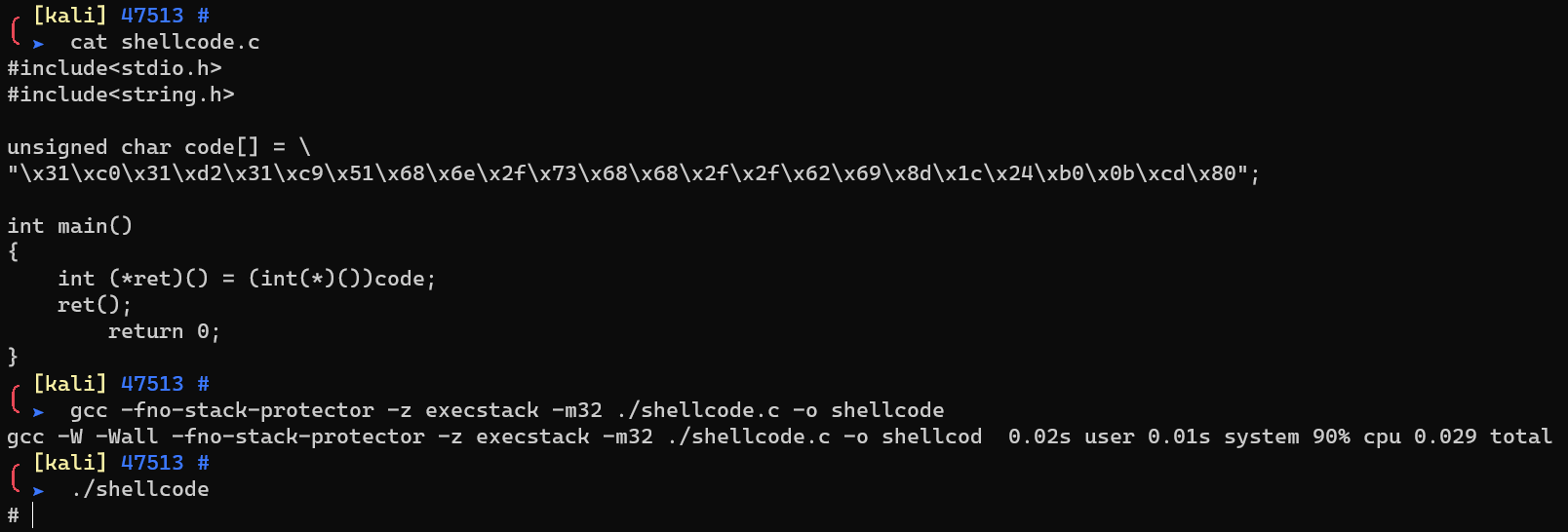
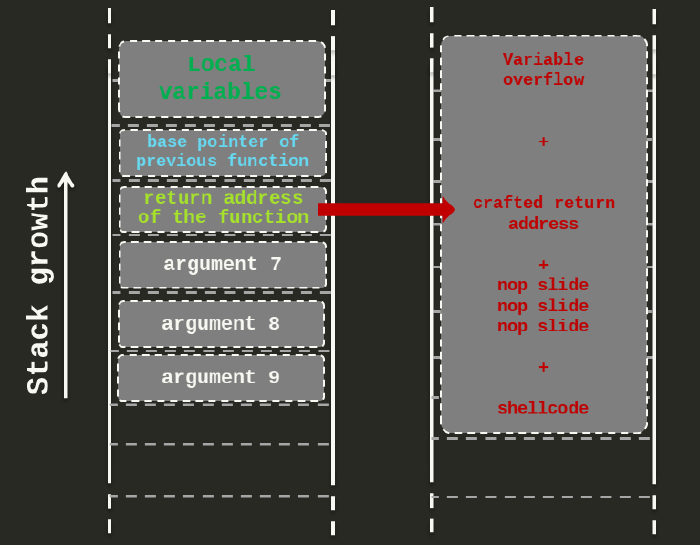
A complete tutorial on the stack-based buffer overflow programming using C code on Linux opensource OS with real demonstration

C++ code (TSF.c) Compiling this code using the command 'gcc TSF.c -z... | Download Scientific Diagram

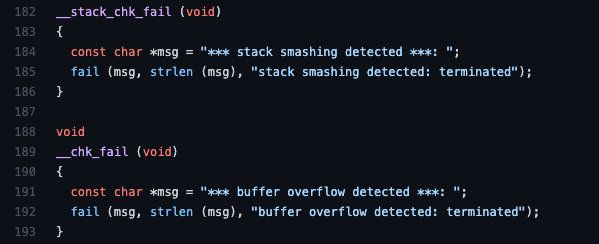
Stack buffer overflow protection 學習筆記– Stack canaries mechanism in User space – SZ Lin with Cybersecurity & Embedded Linux
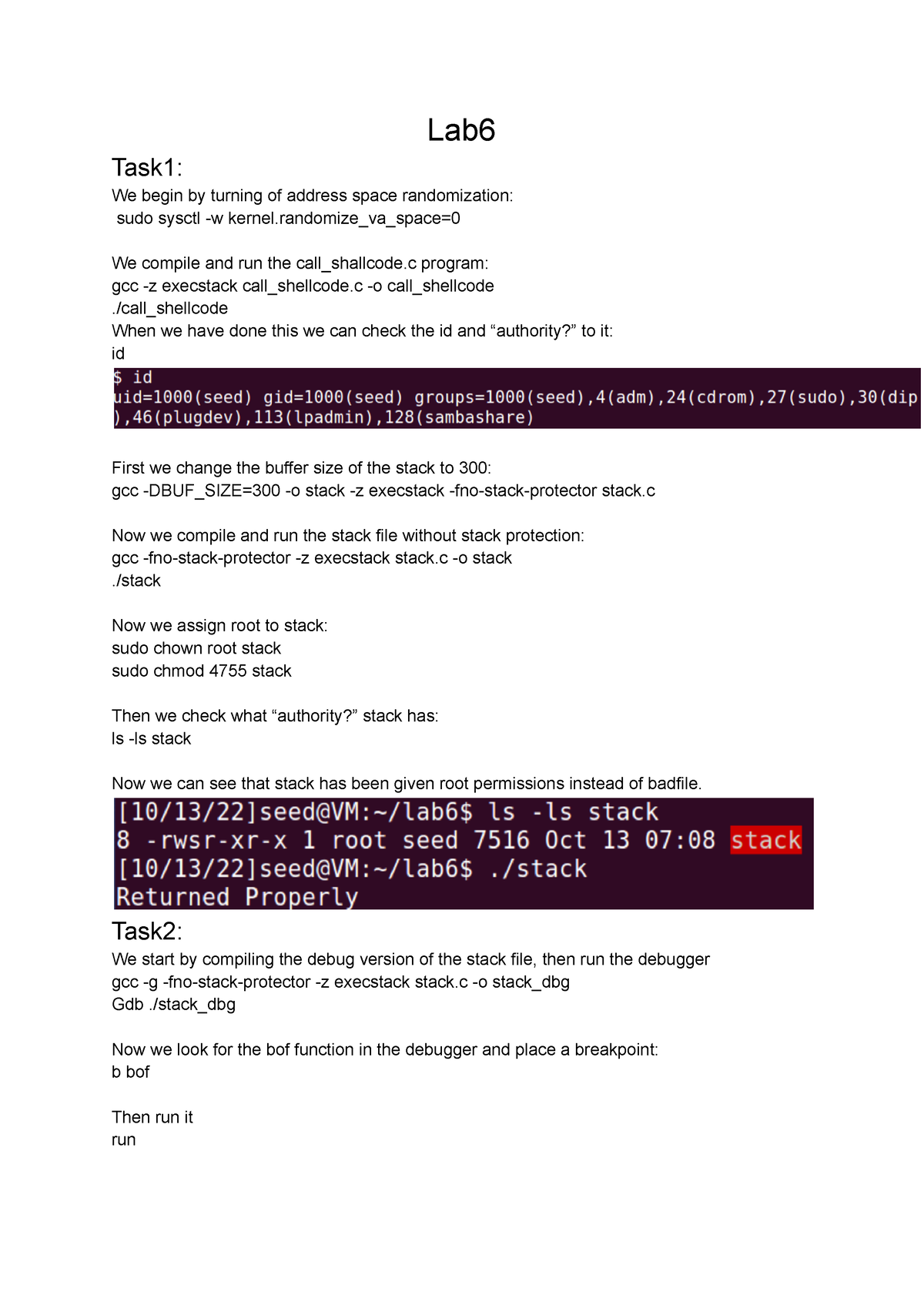
Lab6 - Lab 6 i D0029E, godkänd utan käbbel - Lab Task1: We begin by turning of address space - Studocu

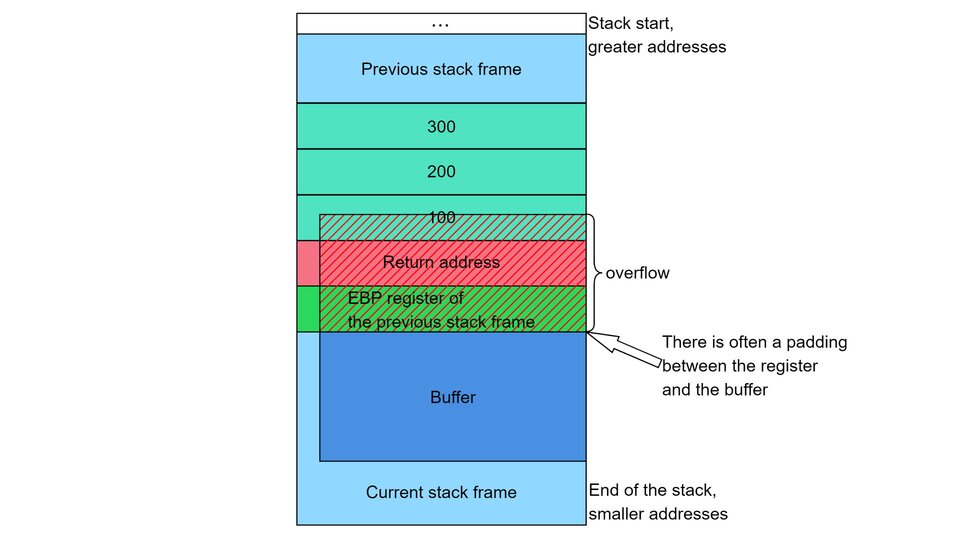
LAB - Chapter 3.2 - Software Security_Buffer_Overflow | PDF | Computer Programming | Software Engineering
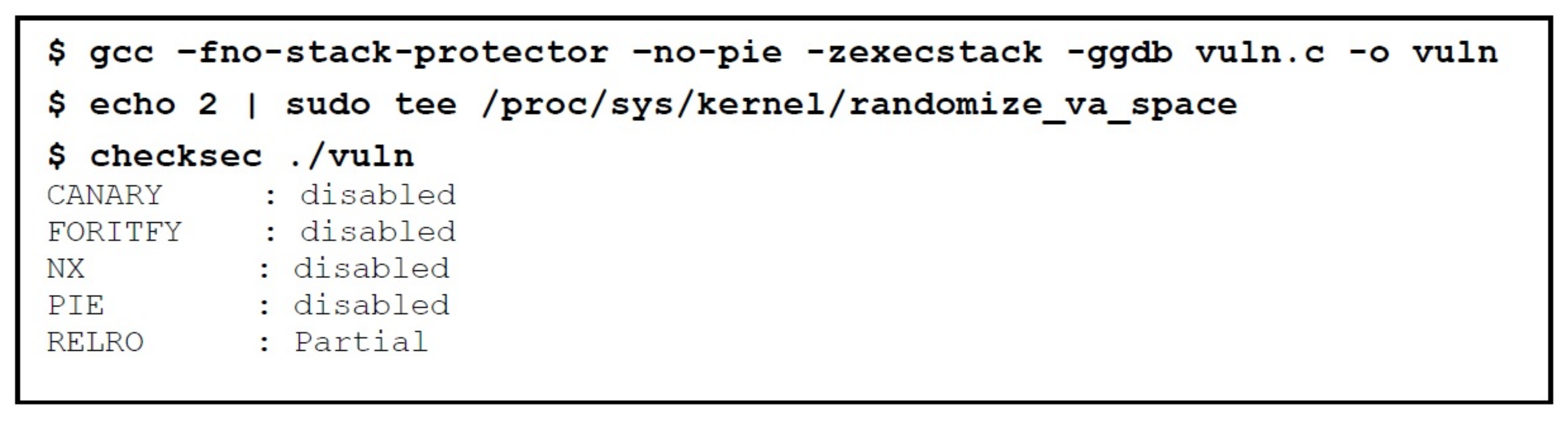
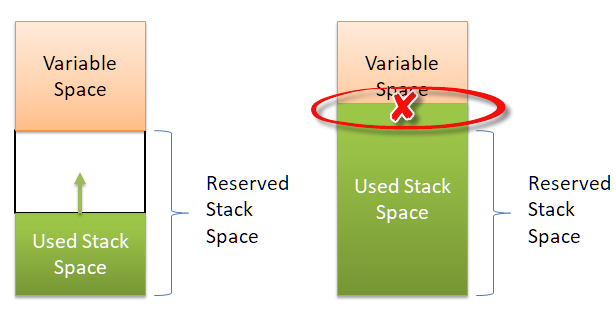
Applied Sciences | Free Full-Text | An In-Depth Survey of Bypassing Buffer Overflow Mitigation Techniques